CVE-2020-13474: NCH Express Accounts- Privilege Escalation
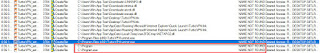
Vulnerable Software: NCH Express Accounts Vulnerability: Privilege Escalation Affected Version: 8.24 and prior Vendor Homepage: https://www.nchsoftware.com/ CVE: CVE-2020-13474 CVE Author: Tejas Nitin Pingulkar Exploit Available: Y es About Affected Software Express Accounts is professional business accounting software, perfect for small businesses needing to document and report on incoming and outgoing cash flow including sales, receipts, payments and purchases. Additional Information NCH express Accounts software allows to access it over the web. A web interface provides 3 types of user Administrator User Viewer The administrator user has access to all modules including Create new invoice, Create new quote, Create new sales order, Create new purchase order, Apply customers payment, View Credit notes, Enter new account payable, view chart of accounts, Make a payment, Receive a payment, Add new item, Add new customer, Supliers list, Add/Edit users User with viewer privile